Disaster recovery as a service or DRaaS sounds dramatic. To allow your business to boom after an unexpected blip, you’ve got to be prepared to weather a disaster recovery storm. That means knowing how to prevent a disaster in the first place, and if the worst happens, knowing how to pick your business up and carry on with minimal disruption. Our disaster recovery guide can help you do that.
In the tech world, we’re experts in acronyms, and we’re well-versed in loaded three-letter-terms. When we’re talking about your disaster recovery plan, you'll want to know what RPO (Recovery Point Objective) and RTO (Recovery Time Objective) both represent and how they can help you create a strategy to keep your business afloat if the worst actually happens.
To allow your business to boom after an unexpected blip, you’ve got to be prepared to weather a disaster recovery storm.
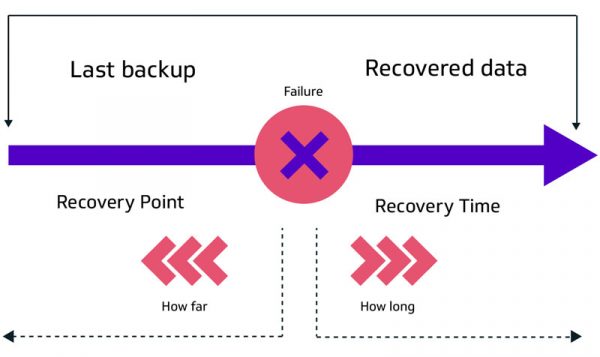
What is RPO (‘Recovery Point Objective)
The Recovery Point Objective refers to the maximum amount data that can be lost taking into account the last time that data was backed up and the point at which that data was lost. For RPO, it’s all about how much data can be lost before it seriously impacts on the ability of your business to function.
What is RTO (‘Recovery Time Objective’)
The Recovery Time Objective is all about the amount of downtime your business will have until it's back up and running and available to customers. As part of a robust disaster recovery plan, RTO focuses on the time it takes for your systems to get back online after your customers or users have been impacted.
How do you prioritise which apps or services should be your focus after a disaster?
There’s no clear-cut ‘one size fits all’ formula for coming up with a disaster recovery plan. Your own business will have its own priorities based on your customer base and how you deal with them.
Some businesses will operate with specific Service Level Agreements (‘SLAs’) around certain processes or customer experiences, which will mean that restoring a particular service will be top of your list of priorities.
Anything centred around the profit of your business is likely to be a critical consideration. You may have carried out a Business Impact Analysis (‘BIA’) as part of your disaster recovery business continuity plan, which will centre around recovering key data that drives your business, and understanding which applications are pivotal to your customers.
Anything centred around the profit of your business is likely to be a critical consideration.
Intercity can be your disaster recovery saviour
How can Intercity help you with working out your RTO/RPO parameters to make sure the impact on your business is minimised?
With our Touch Cloud and Touch Secure platforms, we can manage your servers securely and make sure that your IT is available when you need it most: we work with your RPO and RTO firmly in mind.
With our dedicated data centres and experts managing your infrastructure, your cloud servers are in safe hands: we’re here for you 24 hours a day, 7 days a week and 365 days a year ensuring that your business continuity plan can be implemented as soon as a disaster occurs.
In the event of a hardware failure, your information and projects are stored remotely and can be accessed quickly to keep your staff working and your customers happy.
Contact us at Intercity to help disaster-proof your business and build a solution around your business’ RPO and RTO.
Subscribe to our newsletter
YOU MAY ALSO BE INTERESTED IN:




